INTRODUCTION TO AZURE ACTIVE DIRECTORY
- It integrates with on-premises Active Directory.
- It enables single sign-on with your apps.
- It supports open standards such as SAML, WS-Fed, and OAuth 2.0.
- It supports Azure AD Graph REST API.
Suppose you have an on-premises Windows Server Active Directory environment that you use to enable employees to sign on to intranet apps:
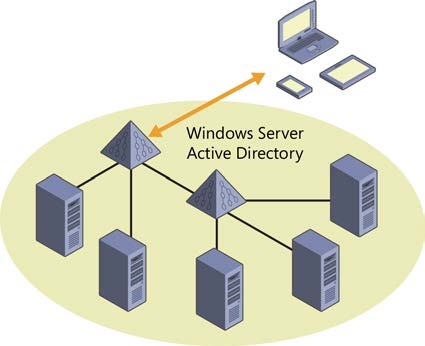
What Azure AD enables you to do is create a directory in the cloud. It’s a free feature and easy to set up.
This directory can be entirely independent from your on-premises Active Directory; you can put any user you want in it and authenticate them in Internet apps.
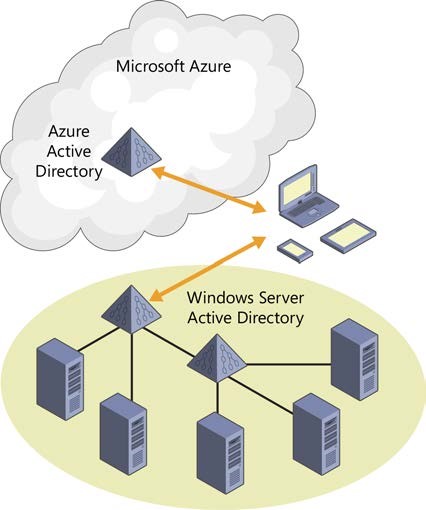
Or you can integrate it with your on-premises AD.
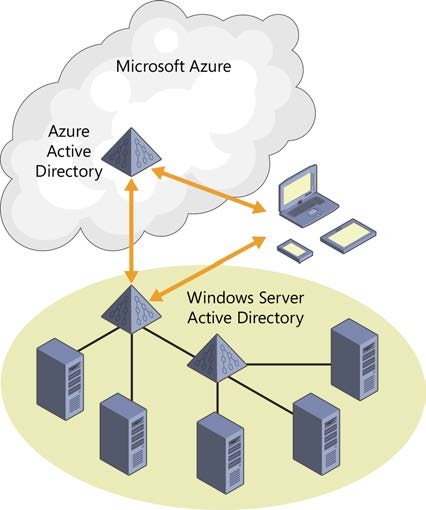
Now all the employees who can authenticate on-premises can also authenticate over the Internet— without you having to open up a firewall or deploy any new servers in your data center. You can continue to leverage all the capabilities of the existing Active Directory environment that you know and use today to give your internal apps single-sign on capability.
Once you’ve made this connection between AD and Azure AD, you can also enable your web apps and your mobile devices to authenticate your employees in the cloud, and you can enable third-party apps, such as Office 365, SalesForce.com, or Google apps, to accept your employees’ credentials. If you're using Office 365, you're already set up with Azure AD because Office 365 uses it for authentication and authorization.

The beauty of this approach is that any time your organization adds or deletes a user, or a user changes a password, you use the same process that you use today in your on-premises environment. All of your on-premises AD changes are automatically propagated to the cloud environment.
If your company is using or moving to Office 365, the good news is that Azure AD will be set up automatically. So you can easily use the same authentication that Office 365 uses in your own apps.
No comments:
Post a Comment